Enabling Fine-Grained Consent with OAuth Rich Authorization Requests (RAR)
In today’s API-driven world, traditional OAuth 2.0 authorization using scopes often falls short when applications require fine-grained and context-specific permissions. This is where OAuth RAR (Rich Authorization Requests) comes in—a powerful extension to OAuth 2.0 that enables precise and structured access requests.
In this technical overview, we’ll explain what OAuth RAR is, how it works, its benefits over traditional scopes, and practical use cases where it shines.
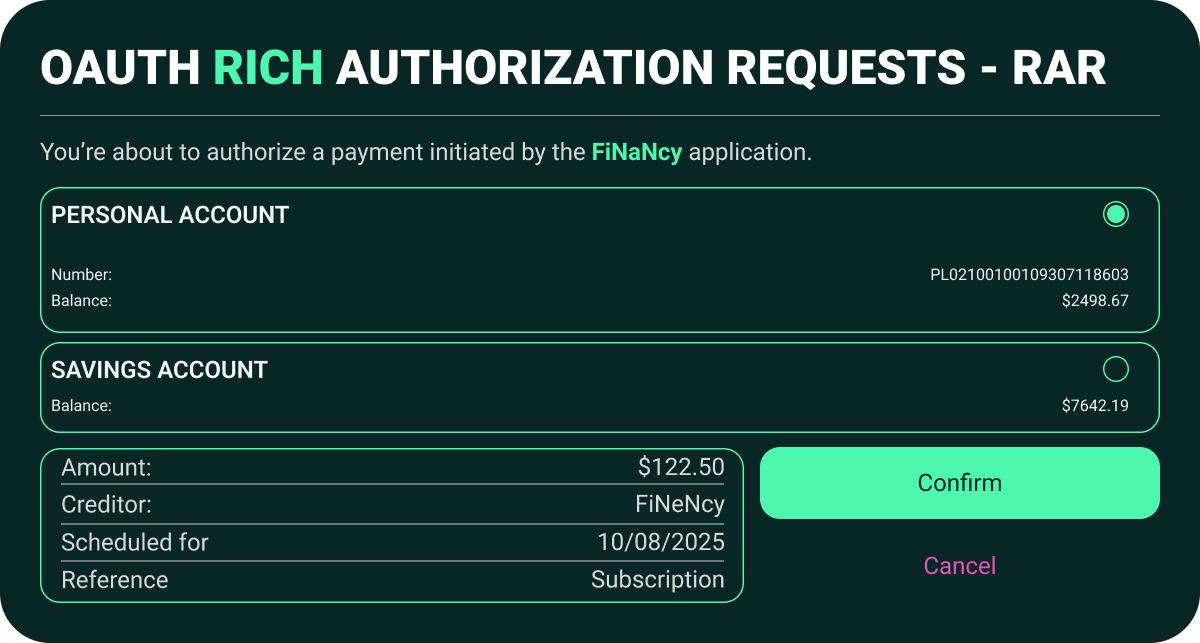
What Is OAuth RAR
OAuth RAR (Rich Authorization Requests) is an official extension to the OAuth
2.0 protocol that introduces a new way for clients to specify authorization
needs in a detailed, structured format. Instead of using simple, space-separated
scope strings, RAR allows clients to send an authorization_details parameter
containing rich, JSON-based authorization information.
This allows applications to request fine-grained permissions that match specific actions, resources, and business contexts—providing better user transparency, stronger security, and greater flexibility.
How OAuth RAR Works
At the core of OAuth RAR is the authorization_details parameter. It is a JSON
array of objects, each defining the precise access the client is requesting.
Each object must include a mandatory type field, with optional attributes such as:
-
locations– The resource or resource server -
actions– The allowed operations (e.g., read, write, transfer) -
datatypes– The type of data being accessed -
identifier– A specific resource identifier -
privileges– The level or type of access -
Custom fields – Any additional fields tailored to the ecosystem
Example: Payment Initiation Authorization
{
"authorization_details": [
{
"type": "payment_initiation",
"locations": ["https://east-bank-union.com/app/api/payments"],
"instructedAmount": {
"currency": "USD",
"amount": "65.50"
},
"creditorName": "FiNaNcy",
"creditorAccount": { "iban": "PL062823001093078721343" }
}
]
}
In this example, the client requests authorization to initiate a payment for $65.50 to a specific merchant and account—something that traditional OAuth scopes cannot express.
Where RAR Fits in OAuth
-
Client builds the authorization request, including the
authorization_details. -
Request is sent to the Authorization Server (AS) using standard OAuth flows (e.g., Authorization Code Flow).
For larger requests or enhanced security, clients can use Pushed Authorization Requests (PAR) or JWT-secured Authorization Requests (JAR).
-
Authorization Server validates the request, interprets the fine-grained details, and displays a consent screen that reflects the exact request.
-
User approves or denies the request based on clear, detailed information.
-
Access token is issued, potentially containing claims or references that reflect the precise permissions granted.
-
Resource servers enforce authorization based on these fine-grained permissions, rather than relying solely on broad scopes.
→ Learn more about JWT-Secured Authorization Requests (JAR)
RAR Key Benefits
Fine-Grained Permissions
OAuth RAR enables clients to request exactly what they need—no more, no less. This reduces the risk of over-provisioning and aligns with the principle of least privilege.
Contextual Authorization
With RAR, clients can include business-specific details in their requests, such as payment amounts, data types, or device actions. This level of detail is not possible with traditional scopes.
Transparent User Consent
Consent screens can display clear, specific information (e.g., “Authorize transfer of €123.50 to Merchant A”)—helping users make informed decisions.
Standardized and Extensible
OAuth RAR is a standards-based approach supported across multiple industries, including financial services, healthcare, and IoT. Its JSON-based structure allows for easy customization and future-proofing.
Enhanced Security
By limiting access to precisely the requested resources and actions, RAR improves both security and compliance, especially in regulated environments.
Real-World Use Cases for OAuth RAR
OAuth RAR is highly relevant in industries and applications that demand precise authorization controls:
| Use Case | Example Authorization Details |
|---|---|
| Open Banking | Initiating a specific payment, accessing a specific account balance |
| Healthcare | Viewing specific medical records, lab results, or device data |
| File Sharing | Requesting read access to one folder, write access to another |
| IoT Devices | Granting control over specific device functions or data streams |
OAuth RAR vs. Traditional OAuth Scopes
| Feature | Traditional Scopes | OAuth RAR |
|---|---|---|
| Data Structure | Space-separated strings | Structured JSON objects |
| Granularity | Coarse-grained | Fine-grained, specific |
| Contextual Information | Limited or absent | Rich and detailed |
| Consent Clarity | Often generic | Highly specific and actionable |
| Extensibility | Difficult to extend | Easily customizable per ecosystem |
Traditional OAuth scopes might suffice for basic use cases, but when applications need precise control, clearer consent, and tighter security, OAuth RAR is the right solution.
Implementation Considerations
To implement OAuth RAR successfully:
-
Authorization Servers must support and validate the authorization_details types and semantics.
-
Clients must be pre-registered or configured to request specific authorization types.
-
Resource Servers must enforce fine-grained permissions based on the access tokens issued.
-
Security best practices recommend using Pushed Authorization Requests (PAR) and/or JWT-secured Authorization Requests (JAR) to ensure request integrity, confidentiality, and protection against injection attacks.
How Raidiam Enhances Fine-Grained Authorization Beyond OAuth RAR
OAuth RAR empowers client applications to request rich, contextual permissions using structured authorization_details. But what if you want even tighter control over which applications are allowed to request certain types of rich authorizations in the first place? This is where Raidiam takes fine-grained authorization even further.
Role-Based Control Over Authorization Requests
In Raidiam, organizations can assign roles to client applications as part of a broader role-based access control (RBAC) model. These roles act as a coarse-grained permission layer, defining what category of actions an application is generally allowed to perform.
Raidiam allows administrators to associate metadata with each role—providing a
mechanism to control which types of authorization_details a client application
is allowed to request based on its assigned role.
Practical Example: Payment Initiation Role
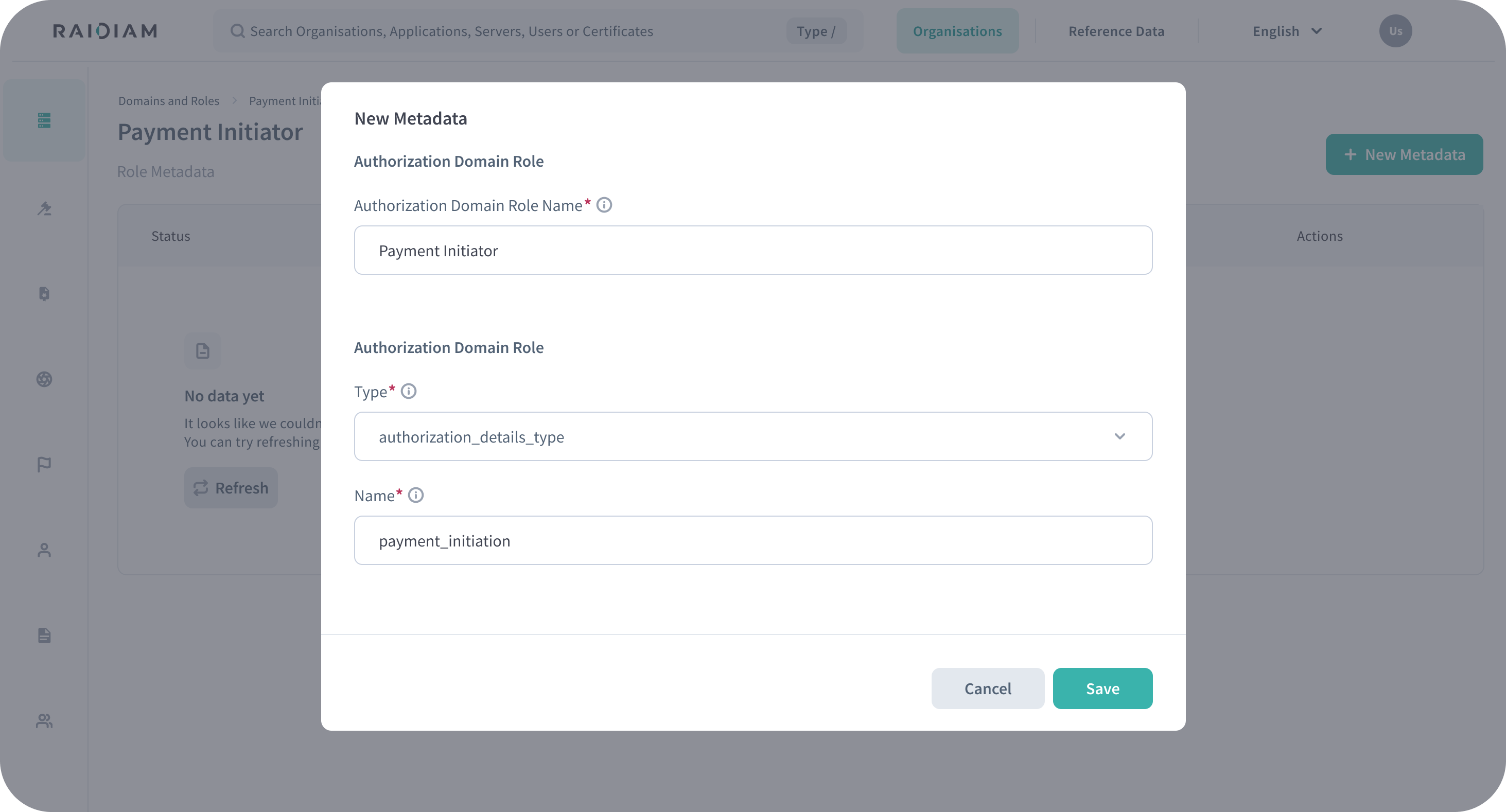
Imagine an ecosystem where only accredited payment service providers (PSPs) are allowed to initiate payments on behalf of users. With Raidiam:
-
A “Payment Initiator” role could be created.
-
This role includes metadata specifying that applications holding this role are permitted to use the
authorization_detailstype:{
"authorization_details": [
{
"type": "payment_initiation",
}
]
} -
Only applications with the Payment Initiator role can send RAR requests containing this
authorization_detailstype. -
Applications without this role will have their requests rejected or ignored by the authorization server.
This model ensures that only authorized and accredited applications can request sensitive or high-risk actions, such as payment initiation, medical data access, or privileged IoT operations.
Benefits of Combining RAR with Raidiam Roles
| Capability | OAuth RAR Alone | OAuth RAR + Raidiam Roles |
|---|---|---|
| Fine-Grained Access Requests | ✅ Yes, via authorization_details | ✅ Yes |
| Contextual Consent Screens | ✅ Yes | ✅ Yes |
| Role-Based Authorization Control | ❌ Not built-in | ✅ Yes—using Raidiam roles and metadata |
| Ecosystem-Level Permission Control | ❌ Requires custom development | ✅ Supported out of the box |
| Security Against Unauthorized Use | Partial—relies on AS/RS enforcement | Strong—enforced at role assignment |
The Pyramid of Layered Authorization: Roles, Scopes, and Rich Authorization Requests
To achieve robust and flexible access control, organizations can apply a layered authorization model, where each layer adds a distinct level of security and precision.
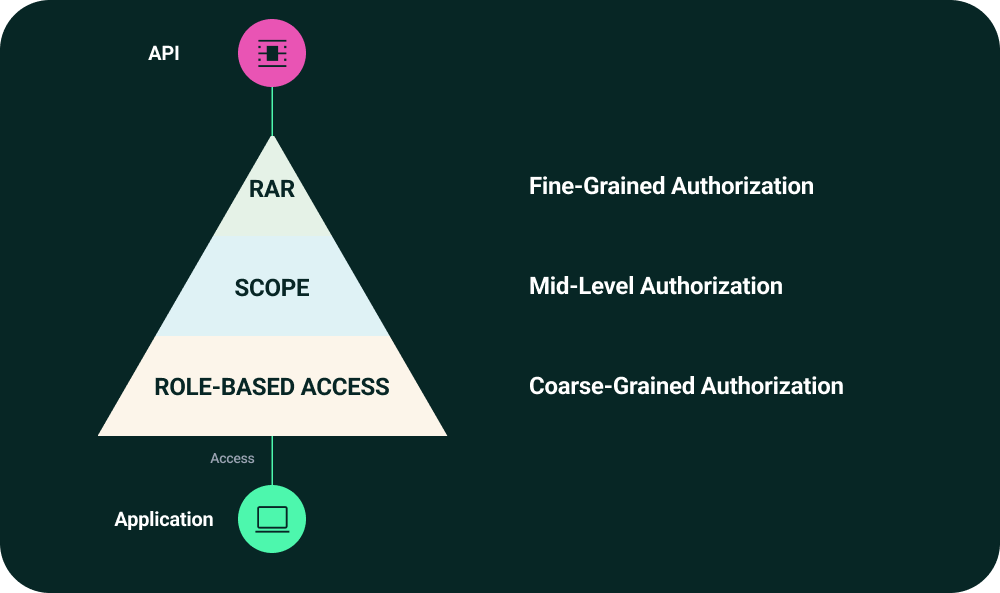
-
Roles (Coarse-Grained Access Control)
Defined and managed by platforms like Raidiam.
Determine who is allowed to request certain types of actions (e.g., only apps with the Payment Initiator role can request payment authorization).
Acts as the first gatekeeper.
-
OAuth Scopes (Medium-Grained Access Control)
Define what categories of access the application requests (e.g., accounts.read, payments).
Standard part of OAuth 2.0.
-
OAuth RAR (Fine-Grained Access Control)
Uses
authorization_detailsto request exact actions, resources, or data (e.g., initiate a €123.50 payment to a specific IBAN).Provides context-rich, transaction-specific authorization.
By combining OAuth RAR with Raidiam’s role and metadata system, organizations can:
-
Provide rich, contextual access requests using standard OAuth mechanisms.
-
Restrict who is even allowed to request certain types of authorizations, adding a layered security model on top of RAR.
-
Ensure that client applications cannot overstep their accreditation or intended function, even if they try to craft complex
authorization_detailsmanually.
This approach delivers the best of both worlds: fine-grained, standardized OAuth authorization with ecosystem-level governance and control provided by Raidiam.
Conclusion
OAuth RAR (Rich Authorization Requests) brings granular, contextual, and standardized authorization to OAuth 2.0. By replacing the limitations of traditional scopes with flexible JSON-based requests, RAR enhances both security and user experience.
Industries like Open Banking, Healthcare, IoT, and Enterprise APIs can benefit greatly from adopting OAuth RAR, enabling more precise control over data access and operations—without sacrificing interoperability or compliance.
As API ecosystems evolve, fine-grained authorization through OAuth RAR is quickly becoming the new standard for secure, transparent, and user-friendly access control.
API Security Report
Helping Enterprises Recognize and Address Critical Risks
More than 80% of organizations are exposing sensitive data with weak API security
Download Now →