Strengthening API Onboarding with Trust and mTLS
APIs don’t stop at access control. Even with roles, scopes, and policies in place, you still need to decide which participants are even allowed to connect. This isn’t about soft notions of trust, but about defining the perimeter: only enrolled, validated organizations and their applications should ever reach the point where tokens or scopes apply.
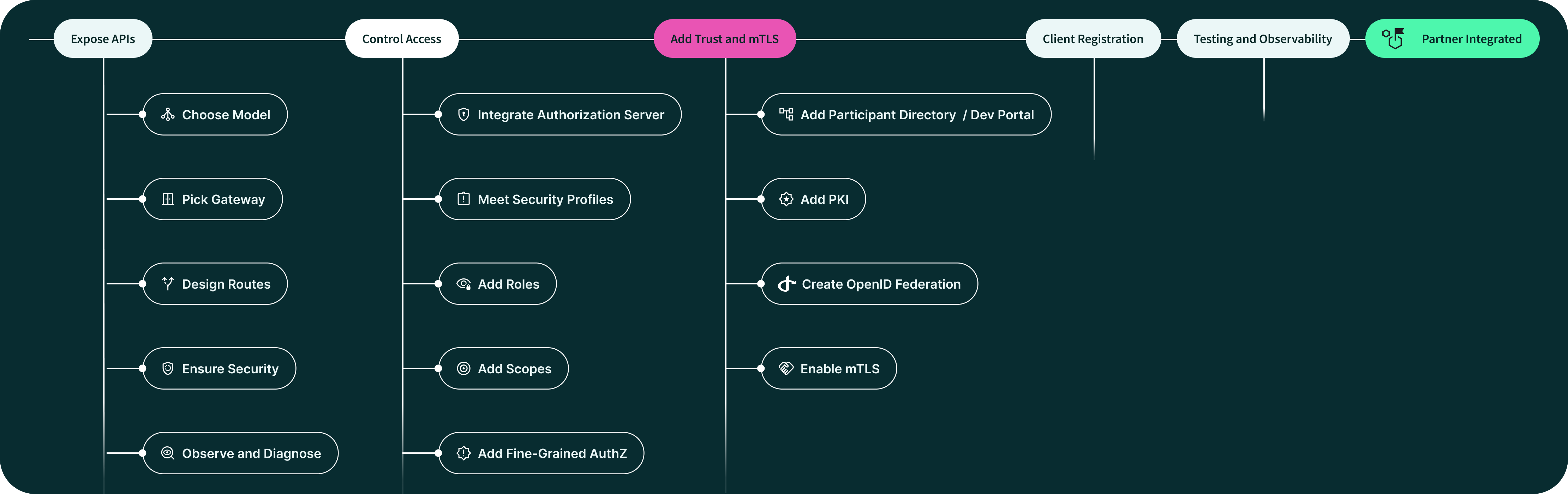
This article continues our series Onboarding Your First Partner in 30 Days. In Exposing APIs the Right Way, we showed why an API Gateway is your first line of defense — the single choke point for TLS termination, token validation, routing, and logging. In Setting Up Access Control for Your APIs, we explored how to enforce scopes, roles, and policies once a client is connected.
Here, we take a step further back and ask an even more fundamental question: who is allowed to connect at all? By combining participant registries, cryptographic trust anchors, and mutual TLS (mTLS), you can define that perimeter and ensure only validated organizations and applications ever reach the point where access control applies.
Establishing the Perimeter for API Onboarding
Defining the perimeter of access isn’t a single control — it’s a layered approach. At minimum, three components need to work together:
-
Participant directories / trust registries — a system of record for who’s in your ecosystem.
-
Cryptographic trust anchors — PKI or OpenID Federation that make enrollment verifiable.
-
Mutual TLS (mTLS) — runtime enforcement of identity and secure transport.
These layers complement each other: the directory defines who, trust anchors make it verifiable, and mTLS enforces it at runtime.
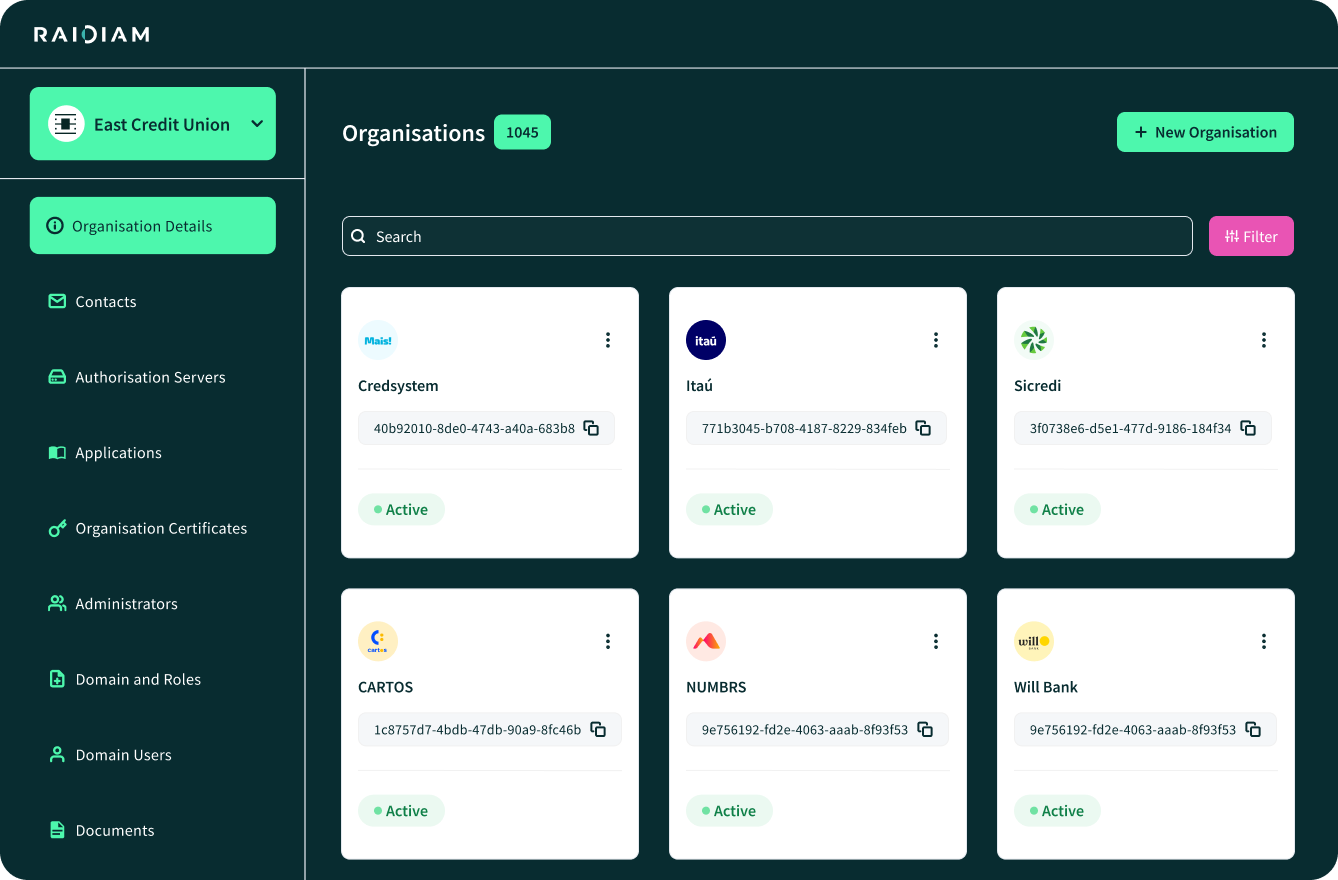
Participant Directories and Trust Registries for Onboarding Partners to APIs
A registry (sometimes called a participant directory or developer portal) is the operational entry point for partners. It ensures that only recognized organizations can onboard, and it captures the technical resources needed for secure communication.
In practice, a registry includes:
-
Organization records — legal entity, identifiers, contacts.
-
Applications and services — registered client IDs, redirect URIs, certificates.
-
APIs and authorization servers — partners may register their own APIs or AS if bilateral communication is needed.
-
Certificates and keys — X.509 certs or JWKS endpoints used for authentication and signing.
-
Role assignments — applications can be granted roles or entitlements here, which directly ties into access control at runtime.
This directory becomes the system of record that downstream infrastructure (gateways, authorization servers, PDPs) consults when enforcing policy. It prevents ad hoc enrollment, provides a single place to revoke or rotate partner access, and ensures access control has a reliable source of truth to pull from.
Cryptographic Trust Anchors for Onboarding Partners to APIs
Directories provide the who, but you need cryptographic roots of trust to make it machine-verifiable. This is where trust anchors come in. They ensure that enrollment isn’t just recorded in a registry, but cryptographically verifiable by your infrastructure at runtime.
Both PKI and Federation serve the same core purpose: they bind a partner’s identity to cryptographic material that can be verified automatically. Together with directories, they form a two-layer model:
-
The registry acts as the governance and enrollment record.
-
The trust anchor ensures that record is cryptographically enforceable.
PKI with X.509 Certificates
In a PKI model, a Certificate Authority (CA) issues X.509 certificates that tie a public key to a client identity. The client generates a keypair locally, creates a Certificate Signing Request (CSR) with its public key and identifiers (CN, SAN, SPIFFE URI, etc.), and the CA signs it. The resulting certificate chains to a trusted root that the API Gateway or Authorization Server recognizes.
When a client connects over TLS, the server requests a certificate. The client presents its certificate and proves possession of the private key by signing handshake data. The server then validates:
-
the certificate chain against its trust anchors,
-
validity and revocation status,
-
required extensions (e.g., EKU
clientAuth), -
and identity mapping via SAN or subject.
This process establishes an encrypted channel and authenticates the client.
For stronger assurance, tokens issued to the client can include a cnf claim
with the certificate thumbprint (RFC 8705). Gateways then verify that the
certificate used for TLS matches the token, binding API access to both
possession of the key and the token.
OpenID Federation
OpenID Federation replaces per-certificate distribution with signed metadata documents. Each organization publishes metadata describing its endpoints, supported features, and public keys. That document is digitally signed with the organization’s private key and linked to a higher-level Trust Anchor.
When your system consumes the metadata, it verifies the digital signature and follows the chain of trust back to the anchor. This creates a machine-readable trust relationship where participants can be authenticated and their capabilities verified, without manual certificate provisioning or bilateral agreements.
Because new participants only need to publish and sign their metadata, federation scales well in ecosystems where partners must onboard dynamically and interoperate securely at large scale.
→ Establish multi-lateral trust between organisations exchanging digital data. Create OpenID Federations with Raidiam. Learn more.Enforcing Trust with mTLS for Partner Onboarding to APIs
Once participants are registered in a directory and cryptographic trust anchors are established, the next step is runtime enforcement: making sure only trusted clients can connect. This is where mutual TLS (mTLS) comes in — it both secures the transport and provides cryptographic client authentication.
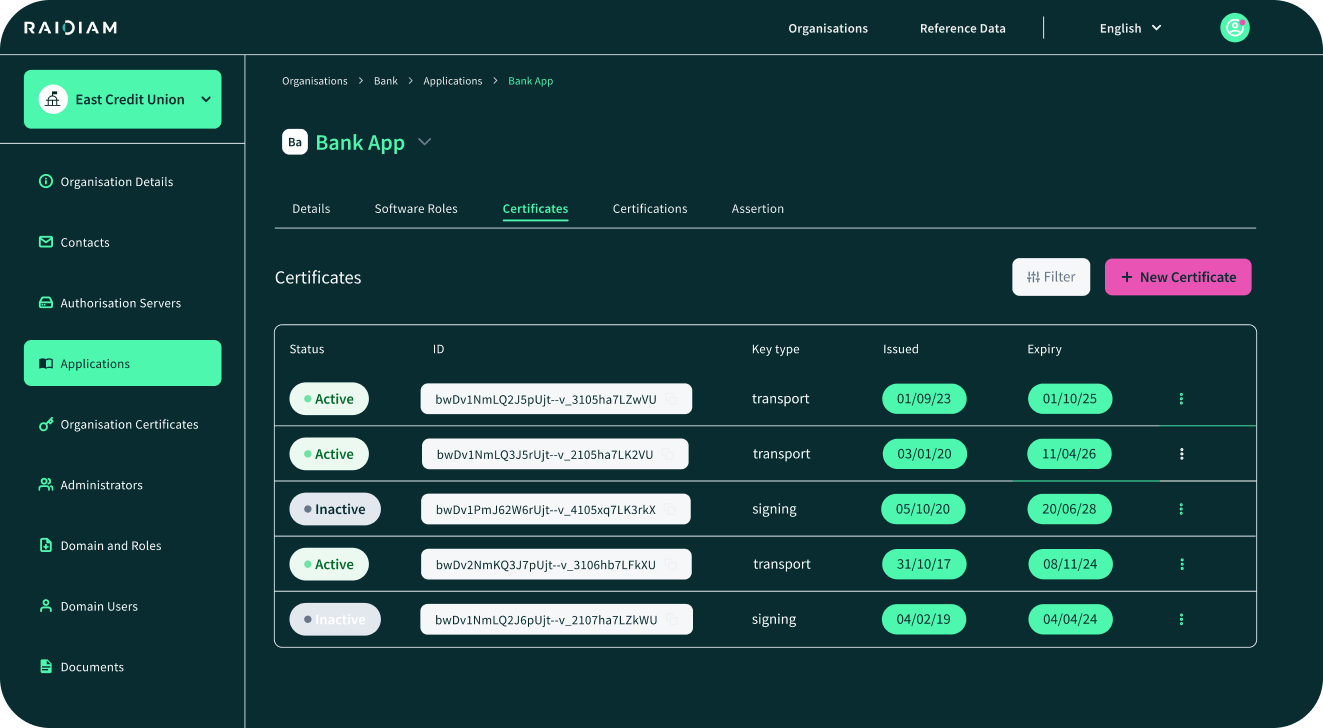
Obtaining Certificates
Certificates are the core of mTLS. You have two primary options:
-
Internal PKI — Your organization acts as a certificate authority (CA). You generate client certificates for partners and maintain a trust anchor that the API gateway recognizes. This allows full control over issuance, revocation, and rotation.
-
External CA-issued certificates — Partners may use certificates from a public/their CA. This is convenient for cross-organization trust, but certificates must conform to industry standards and lifetimes mandated by the root CA
When deciding between internal and external PKI, consider:
-
Control vs interoperability: Internal PKI gives full control; public CA certificates ease partner adoption.
-
Revocation and rotation processes: Internal PKI allows faster response to compromised keys.
-
Lifecycle automation: both approaches require automation at scale.
Configuring Certificates on Your Authorization Server
When onboarding partner applications, your Authorization Server (AS) becomes the gatekeeper for secure connections. It must enforce TLS and require mTLS-based client authentication to ensure only enrolled clients can request tokens. Key considerations include:
Enable mTLS
-
Enable TLS for all endpoints
-
Require HTTPS for token issuance, introspection, and revocation endpoints.
-
Prefer TLS 1.2+ or 1.3, disable legacy ciphers, and enforce strong cipher suites.
-
-
Enforce mTLS client authentication
-
Configure the AS to request and validate client certificates during the TLS handshake.
-
Map validated certificates to internal client IDs or roles. This ties each certificate to a known participant in your directory/trust registry.
-
Reject any request where the certificate is invalid, expired, or unrecognized.
-
Certificate Storage and Access
-
Store your server’s private key and signing certificates securely (HSM, encrypted filesystem, or secret manager).
-
Maintain the CA bundle used to validate partner certificates; include intermediates as needed.
-
Rotate server certificates and trust anchors periodically to reduce risk from key compromise.
Integration with Token Issuance
-
If issuing mTLS-bound access tokens, include the certificate fingerprint in the token’s
cnfclaim. -
Downstream gateways will validate this
cnfclaim against the client certificate presented during TLS, ensuring tokens cannot be replayed by an unauthorized party.
Operational Considerations
-
Monitor certificate expiration dates and automate renewal workflows.
-
Implement logging of TLS handshakes, certificate fingerprints, and validation outcomes for auditing and troubleshooting.
-
Consider fallback mechanisms for high availability: cached trust anchors or redundant validation services to handle transient CA outages.
Align with Regulatory/Industry Mandates
-
For public CA-issued certificates, account for CA/Browser Forum limits on certificate lifetimes (currently capped at 47 days).
-
Automate issuance and rotation to prevent service disruption for partner applications.
Configuring Certificates on the Gateway
The API Gateway must verify client certificates against a trusted CA bundle. Key steps:
-
Import the CA chain — include all intermediate and root certificates required to validate client certificates.
-
Enable client certificate verification — configure the gateway to request a client certificate on TLS handshake.
-
Optional certificate mapping — some gateways allow mapping a client certificate to an internal client ID or role.
Many gateways also support dynamic truststores, allowing new certificates to be added without downtime.
Storing and Managing Certificates
Proper storage and lifecycle management is critical:
-
Private keys must be encrypted at rest and accessible only to the owning service or agent.
-
Certificates can be cached locally for validation performance but must be periodically refreshed.
-
Intermediate and root certificates in the gateway truststore must be rotated before expiry to avoid validation failures.
-
Monitoring and alerting for certificate expiry is essential.
Certificate Lifetimes and Automation
From March 2025, TLS certificate lifetimes are being progressively reduced, with a final maximum lifetime of 47 days, per the CA/Browser Forum mandate. For organizations relying on public CA-issued certificates for mTLS, this creates operational challenges:
-
Certificates must be issued, rotated, and deployed frequently.
-
Manual processes do not scale and increase the risk of outages or misconfiguration.
-
Automation is mandatory — integrate issuance, distribution, and rotation with CI/CD pipelines or secret managers.
-
Monitoring and alerting on expiry dates is critical.
Automation ensures mTLS enforcement remains reliable and prevents partner outages caused by expired or misconfigured certificates.
Gateway Verification and Token Binding
With certificates installed:
-
The gateway validates the client certificate chain during TLS handshake.
-
If using mTLS-bound tokens, the Authorization Server issues tokens containing a
cnf(confirmation) claim with the certificate fingerprint. -
The gateway verifies that the token’s
cnfclaim matches the presented certificate.
This ensures that only the legitimate holder of the private key can use the token — preventing token replay or theft from compromising security.
Key Operational Considerations
-
Clock synchronization — TLS validation relies on accurate time; gateway and client clocks must be synchronized.
-
Certificate revocation — Maintain CRLs or use OCSP to invalidate compromised certificates.
-
Fallback and redundancy — Implement high availability for gateways and truststores; cached trust anchors can temporarily sustain operations during transient CA outages.
-
Auditing and logging — Log certificate fingerprints, client IDs, and validation results for audit and incident response.
Putting It Together
Establishing a secure partner onboarding perimeter requires coordination across multiple layers:
-
Participant Directory / Trust Registry – defines who is allowed to participate. Every partner organization, application, and API is enrolled here, with associated roles, certificates, and metadata. This becomes the authoritative source for access decisions.
-
Cryptographic Trust Anchor – ensures that enrollment is machine-verifiable. PKI or OpenID Federation binds each partner to cryptographic material, enabling deterministic validation of identity at runtime and preventing spoofing or impersonation.
-
Mutual TLS (mTLS) – enforces the perimeter in real time. Only clients presenting valid certificates anchored to your trust model can establish a TLS connection with the Authorization Server or API Gateway. Combined with optional mTLS-bound tokens, this guarantees that only the legitimate key holder can access protected resources.
Layering the Controls
-
Enrollment and governance live in the registry.
-
Verification and cryptographic assurance are handled by trust anchors.
-
Runtime enforcement is provided by mTLS at both the AS and gateway.
Access control—roles, scopes, and policies—applies only after a participant has passed this perimeter. Together, these layers form a defensible, auditable, and scalable trust model, ensuring that your APIs are accessible exclusively to validated partners and that every request carries verifiable proof of identity.
Practical Guide
Onboard Your First Partner in 30 Days - No Fluff, Just Code
Get the practical developer playbook with weekly steps, real configs, and copy-ready code to build, secure, and distribute your APIs fast.
Access Now →