Enabling Partner Client Registration
Once organizational trust (PKI / OpenID Federation) is established, the next must-have piece is a way for partner applications to be registered in your Authorization Server (AS). Registration binds metadata (redirect URIs, keys, scopes, etc.) and credentials to a partner app, so your AS can enforce policies, authentication, and access control reliably.
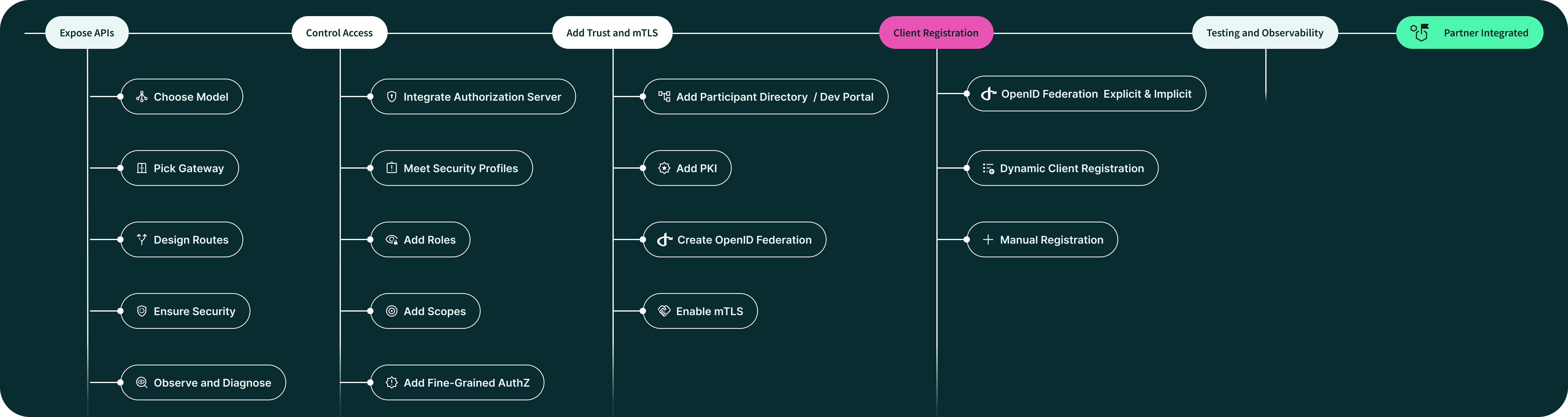
This article continues our Onboarding Your First Partner in 30 Days series. Previously, we covered API Gateway fundamentals, access control, and trust & mTLS to ensure only validated organizations and applications reach your APIs.
The next step is to register partner applications in your Authorization Server (AS). Client registration defines the metadata, keys, and policies an app needs to request tokens and call your APIs.
There are four main models in practice:
-
OpenID Federation — preferred, metadata-driven registration that can be fully automatic. Some deployments also enable explicit federated registration via an endpoint.
-
OAuth 2.0 Dynamic Client Registration (DCR) — standardized API-based registration, but less integrated with federation trust.
-
Manual registration — adding apps via UI or admin API, often through a developer portal.
OpenID Federation Client Registration for Partner Onboarding
OpenID Federation automates client registration via signed metadata and
federated trust chains, enabling secure, policy-driven onboarding at scale. Each
client (Relying Party, RP) publishes an entity_configuration — a signed JWT
containing application metadata such as redirect URIs, grant and response types,
application type, display name, and cryptographic keys (via jwks_uri or inline
jwks). The configuration also includes authority_hints, pointing to the
parent authorities that vouch for the RP.
Intermediate Authorities may issue subordinate statements, effectively certifying the RP metadata and linking it to the top-level Trust Anchor. The Authorization Server (AS, or OP) consumes these statements, validates the cryptographic chain, and provisions the client if it meets local and federation policies.
Automatic Registration
In automatic mode, the RP simply initiates an OpenID Connect flow using its
entityID as client_id. The AS fetches the RP’s entity configuration,
retrieves subordinate and anchor statements, validates signatures and
expirations, and enforces policy before creating or updating the client record.
Explicit Federated Registration
Some deployments expose a federation_registration_endpoint where the RP POSTs
its entity statement (as a JWT or JSON trust chain). The AS validates the chain
against the Trust Anchor, enforces registration policy, and responds with
confirmation and—if required for legacy compatibility—a client_id and
client_secret.
Trust Chain Validation
Validation is recursive: the AS traverses from the RP through any intermediaries to the Trust Anchor. At each hop, it checks JWT signatures, algorithm support, expiration, authority references, and compliance with policy (permitted grant types, supported algorithms, trusted keys). Registration is rejected if any statement is missing, expired, revoked, or invalid.
Policy Enforcement
Even within a federation, the Authorization Server does not blindly accept every
field published by a client. Instead, it evaluates the metadata against local
and federation-level policy. Unsupported or non-compliant values — for example,
disallowed redirect_uris, weak signature algorithms, or grant types not
enabled for partners — can be filtered out or overridden. The AS advertises its
supported values and requirements through its own entity statement and OIDC
metadata, ensuring that partners know upfront what will be enforced.
Key Management and Rotation
Clients authenticate with asymmetric keys that are embedded directly in their
entity statement, either inline (jwks) or via a hosted jwks_uri. Rotation is
straightforward: when a partner publishes new keys, the AS fetches the updated
entity statement during re-resolution and updates the client record accordingly.
If a key is revoked, compromised, or replaced, the trust chain validation will
naturally fail for the old material and accept the new one, with no manual
intervention required. In practice, this means that federation enforces key
hygiene continuously.
Error Handling
Registration may fail for several reasons: invalid or expired statements, broken
trust chains, unsupported algorithms, or policy violations. The AS must make
these failures transparent to developers by returning structured error responses
(e.g., JSON problem details) and appropriate HTTP status codes (400 for bad
metadata, 401/403 for invalid trust). This clarity is critical in federated
environments where multiple parties — RP, intermediaries, and Trust Anchor — all
play a role in successful onboarding.
Endpoint Discovery
Every participant in the federation exposes a /.well-known/openid-federation
endpoint where its entity statement can be retrieved. The AS uses this endpoint
both for automatic discovery and for explicit registration flows. In turn, the
AS itself must publish its own metadata, declaring support for automatic and/or
explicit federation flows in client_registration_types_supported and
advertising the federation_registration_endpoint when applicable.
Trust Marks and Dynamic Policy
Some ecosystems enhance federation with Trust Marks — additional signed JWTs embedded in the entity statement that certify compliance with standards or participation in regulated programs. An Authorization Server can use these to enforce differentiated policy: for instance, allowing only clients with a “PSD2-compliant” mark to access payment APIs, or granting stronger scopes to certified healthcare apps. This allows trust to be expressed dynamically at runtime, not only through static registration data.
Deregistration and Federation Exit
Client registration in federation is inherently dynamic: it only remains valid as long as the trust chain resolves cleanly. If an entity statement expires, an authority revokes its subordinate, or an organization exits the federation, the chain breaks and the AS immediately treats the client as deregistered. From a security perspective, this makes deregistration automatic and tamper-resistant. Operationally, the AS should also log deregistration events for audit and compliance, so administrators can track why and when a client lost access.
OAuth 2.0 Dynamic Client Registration (DCR) for Partner Onboarding
OAuth 2.0 Dynamic Client Registration, defined in RFC
7591, provides a standardized
API for onboarding client applications without manual preregistration. Instead
of filling in a portal form, a client sends a POST to /register with its
desired metadata: redirect URIs, grant and response types, authentication
methods, and public keys (either inline in a JWKS or hosted at a jwks_uri).
In regulated or controlled environments, the request may also include an initial access token to authenticate the caller or a signed software statement that binds the client metadata to a trusted issuer. These artifacts prevent unauthorized or rogue clients from self-registering.
Registration Flow
When the AS receives a registration request, it first validates authenticity — by verifying the initial access token or validating the software statement against its issuer. It then performs metadata and policy checks: ensuring redirect URIs use HTTPS, grant types are permitted, and requested algorithms match server capabilities. Unsupported values may be replaced with defaults or stripped out entirely.
If the request passes, the AS provisions a new client: generating a client_id,
optionally issuing a client_secret for confidential clients, and returning a
registration access token. This token is crucial — it authorizes the client
to update its metadata, rotate credentials, or de-register itself via the
management endpoint (RFC 7592). Under
the hood, the AS stores the client record and metadata, making it available for
subsequent authorization requests.
Technical Flow Diagram
Lifecycle and Governance
The registration access token is both powerful and sensitive: whoever controls it can manage the client’s lifecycle. Best practice is to rotate it periodically and store it securely. Metadata updates (such as adding new redirect URIs or rotating keys) flow through this endpoint, while de-registration requests cleanly remove the client from the AS.
DCR deployments can be hardened with additional controls: limiting who can register by requiring pre-issued tokens, restricting access by network or developer identity, or enforcing continuous compliance checks on metadata.
Error Handling
Errors are communicated through structured JSON responses with clear codes and descriptions, such as invalid URIs, unapproved software statements, or policy violations. This feedback loop allows developers to adjust their metadata quickly and resubmit, reducing friction during onboarding.
Manual Registration
The oldest model: partners (or admins on their behalf) manually enter application details in a portal or UI. While simple and familiar, this doesn’t scale, is error-prone, and introduces security gaps (e.g., misconfigured redirect URIs, expired keys). Manual registration should be a fallback option only.
Choosing the Right Model
| Model | How it Works | Trust Source | Strengths | Weaknesses | Best Fit |
|---|---|---|---|---|---|
| OpenID Federation (Automatic) | AS consumes signed org metadata with client details and provisions clients automatically. | Trust Anchor → org-signed metadata | Fully automated, low error rate, scales to many orgs. | Requires federation support and setup. | Large ecosystems where partners join dynamically. |
| OpenID Federation (Explicit) | Partner submits metadata to a secure endpoint; AS validates org via federation before creating client. | Trust Anchor + federation metadata | Flexibility to add new apps on demand while preserving org-level trust. | Slightly more operational overhead than automatic federation. | Federated ecosystems needing dynamic per-app registration. |
| OAuth 2.0 DCR | Client calls /register API with metadata; AS issues client_id. | AS-local validation + optional policies | Standards-based, supported by many AS implementations. | Lacks built-in org binding; extra validation/policy layers required. | Bilateral/trusted ecosystems with limited participants. |
| Manual Registration | Admin or partner enters app details in UI/portal. | Admin trust | Familiar, no technical setup needed. | High error rate, doesn’t scale, lifecycle management is manual. | One-off apps, testing, or ecosystems without automation. |
The most important rule: always link clients back to their parent organization in your participant directory or registry. This ensures policy enforcement, auditability, and lifecycle management (rotation, revocation, de-registration).
Linking Registered Clients to Organization Identity
Client registration cannot exist in isolation — every client must be linked back to the partner organization it belongs to. Without this, you can’t reliably enforce access control or maintain audit trails.
In practice, the linkage works like this:
-
Each organization has a unique identifier in your participant directory or trust registry.
-
Every client registration — whether created via OpenID Federation, explicit preregistration, or DCR — must carry or be associated with that identifier.
-
The Authorization Server stores a mapping from
client_idtoorg_id.
This mapping becomes the backbone for policy enforcement (quotas, billing, role assignments) and auditability, letting you answer questions like: Which organization invoked this API through which client?
Validation and Lifecycle Considerations
Registration is just the starting point. To be secure and sustainable, client onboarding must be reinforced by ongoing validation and lifecycle management. Developers and operators should enforce at least the following practices:
-
Redirect URI validation: URIs must exactly match registered values. Wildcards should be permitted only under strict policy.
-
Key material checks: Public keys must meet algorithm and size requirements, and JWKS endpoints must be reachable and trustworthy. Reject weak algorithms outright.
-
Rotation support: Clients need a way to rotate credentials; the AS must accept new keys and handle expirations gracefully.
-
De-registration and disablement: Provide clear processes to revoke or disable clients, particularly when an organization exits the ecosystem.
-
Metadata freshness: In federation, respect TTLs and re-validate signatures by periodically fetching metadata.
Together, these safeguards ensure that a registered client stays compliant and secure over its lifecycle.
Summary
Federation-driven client registration should be the default path: it
automates onboarding and embeds trust into the process. When federation isn’t
available, fall back to DCR, but enforce stricter validation and always maintain
the client_id → org_id linkage.
Finally, treat registration as the beginning of an ongoing relationship. Build lifecycle processes for key rotation, de-registration, and metadata refresh — because onboarding partners securely is not just about day one, but about keeping trust intact over time.
By now, you’ve seen how client registration works across Federation, DCR, and manual models — and why linking every client back to its organization identity is critical for security and scale. Ready to put this into practice? Check out our Onboard Your First Partner in 30 Days guide, a developer playbook with weekly steps, real configs, and copy-ready code to help you build, secure, and distribute APIs fast.
Practical Guide
Onboard Your First Partner in 30 Days - No Fluff, Just Code
Get the practical developer playbook with weekly steps, real configs, and copy-ready code to build, secure, and distribute your APIs fast.
Access Now →