Building Access Control for Agentic AI with OpenID Federation
As agentic AI systems proliferate–from autonomous task agents to intelligent orchestration engines–the question of trust evolves from “who is the user?” to “which agent is acting, under what authority, and how can we verify its intent, identity and scope of action?”.
Traditional human-centric identity models break down when autonomous agents invoke APIs, delegate to sub-agents, and operate across domains. OpenID Federation provides the architectural foundation to restore order — a standardized, cryptographically verifiable framework for governing agent identities, registration, discovery, and lifecycle. It enables agents to authenticate and authorize as independent, auditable entities within distributed systems.
In this post we explore: how agentic AI demands enhanced identity and trust infrastructure, how OpenID Federation addresses those demands, and the design patterns for integrating them in practice.
Federation Use Cases in Agentic AI Ecosystems
OpenID Federation does more than solve technical trust resolution — it defines how agentic ecosystems can be built, governed, and expanded with consistent assurance. The standard enables a range of deployment scenarios where agents act as autonomous participants but remain bound to cryptographic, policy-driven control.
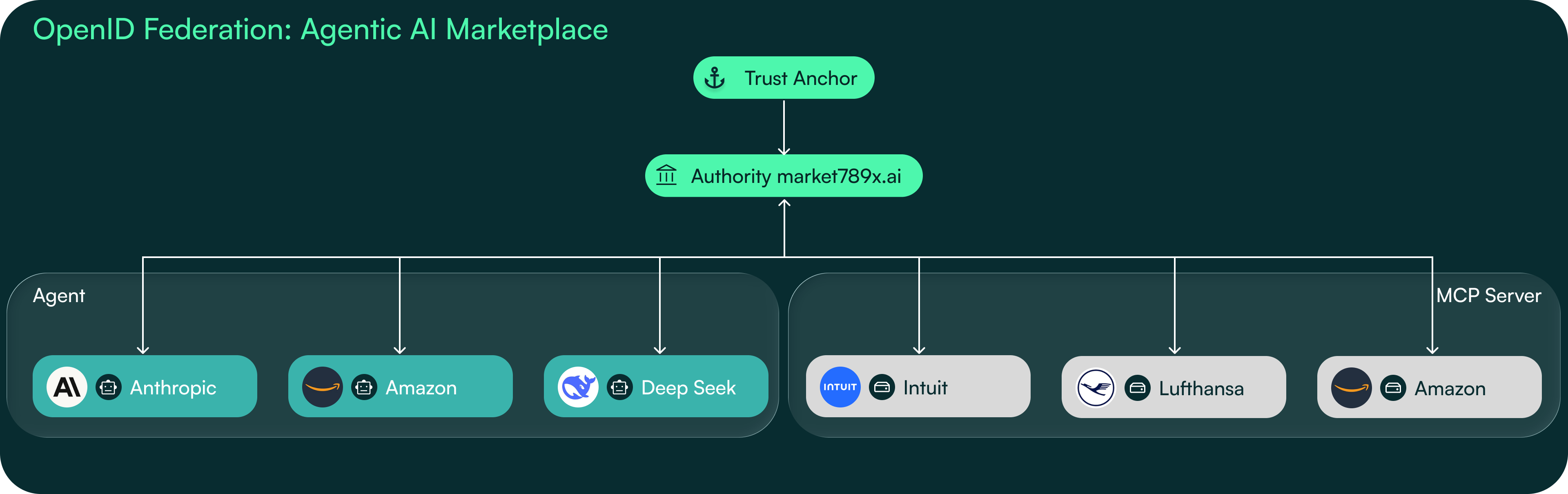
Agentic AI Marketplace
An organization or consortium can operate a trusted catalogue of accredited agents. Each agent or host publishes signed metadata that attests to its identity, capabilities, and compliance level under an approved trust anchor. Integrators and developers can then discover these agents programmatically through the federation, verify their metadata signatures, and onboard them without manual credential exchange. The marketplace becomes a curated ecosystem of interoperable, verifiable agents — each discoverable and consumable via standard federation endpoints rather than proprietary registries.
Internal Agentic AI Ecosystems
Within a single organization, federation enables the creation of an internal agentic AI ecosystem. Every agent — from automation bots to data-processing assistants — can be registered under the enterprise’s trust anchor, inheriting centrally defined policies, certificate profiles, and allowed scopes. Access to internal APIs, datasets, or SaaS services can then be governed through federation metadata rather than static configuration. The result is full visibility and control over what agents exist, what they can access, and who operates them, while preserving agility for development teams to deploy new autonomous capabilities safely.
Multi-Domain and Partner Ecosystems for Agentic AI
As organizations scale, the same model extends outward into multi-domain and partner ecosystems. A global enterprise can federate its business units, partners, and customers under separate but linked trust anchors. Each domain maintains local policy control — defining which agents are approved, what scopes are valid, and which external trust sources are accepted — while interoperability across domains remains cryptographically guaranteed. Agents can therefore operate across internal and external boundaries, with each interaction verified through standard federation discovery and signed metadata rather than custom bilateral integrations.
Why Agentic AI Needs More Than Classic Identity/Access
Agentic AI — here defined as software agents that can autonomously invoke APIs, make decisions, spawn sub-agents and act with minimal human intervention — poses three distinct trust challenges:
-
Identity at the agent level: Unlike a human user, an agent may not map neatly to a user account. It needs its own cryptographic identity, lifecycle, and audit trail.
-
Cross-domain and dynamic operations: Agents may operate across organizational boundaries, call external services, integrate new APIs, and delegate to other agents. Static trust relationships (e.g., pre-shared credentials) do not scale.
-
Delegation and provenance: An agent may create sub-agents, delegate tasks, escalate privileges, or act on behalf of another system. Ensuring traceability, controlling blast radius, and enforcing policy boundaries requires a trust fabric beyond basic OAuth access tokens.
What You Need to Build to Secure Agentic AI Access
Thus, for secure deployment of agentic AI systems, one must build:
-
Cryptographically anchored identities for agents.
-
Metadata and operational context (capabilities, permissions, lifecycle) associated with those identities.
-
A trust model that supports discovery, verification and governance across domains and organizations.
-
Lifecycle management: onboarding, rotation, revocation, delegation control, audit, and provenance.
These requirements align well with existing security standards — but only when adapted and extended for the agentic context.
From Identity to Trust: OpenID Federation in Agentic Context
OpenID Federation is an extension of the OpenID Connect (OIDC) / OAuth 2.0 paradigm that introduces a trust-fabric layer: signed metadata, trust anchors, federated discovery and delegation of authority. In an agentic AI context, this allows agents (or their supervising services) to register, discover and verify one another automatically rather than via manual trust configuration.
Core Components and Flows
-
Trust Anchors: At the top layer sits a trust anchor (or anchors) which define cryptographic roots, policy constraints (e.g., supported algorithms, credential requirements).
-
Federation Operators: Operators delegate trust from the anchor, manage participant registries, define metadata constraints and policy domains.
-
Federation Entities: These are the participants: identity providers, relying parties, API agents, sub-agent services. Each publishes signed metadata describing endpoints, keys, capabilities and policy statements.
1. Agent Registration
-
An agent (or its host service) obtains a federated identity by registering with a federation operator.
-
It publishes metadata: agent ID (entity ID, URI or DID-like identifier), supported endpoints, certificate/key fingerprints, token endpoint, scopes, delegation relationships, allowed APIs.
-
The hosting service obtains a signed metadata statement endorsed (directly or via delegation) by the federation operator.
2. Discovery & Verification
-
When Service A receives a request from Agent X (issued by Host H), Service A resolves the metadata endpoint of Host H via the federation tree, verifies the signature, checks certificate chains, policies, and ensures that Agent X is permitted to call the requested API/scope.
-
Service A may validate mTLS client-cert bound JWT, check the issuer claims, and cross-validate against the federation metadata registry.
3. Delegation & Sub-Agent Lifecycle
-
If Agent X spawns Agent Y, their metadata includes delegation relationships: e.g. “Agent Y is a sub-agent of Agent X” or “hosted by Host H under delegation policy P”.
-
The federation metadata captures delegation constraints: e.g., maximum depth, allowed scopes, time-to-live for sub-agents, required audit-logging obligations.
4. Policy Enforcement & Trust Governance
-
The federation operator defines policy statements in metadata (or via separate policy endpoints) that govern algorithm support (e.g., signing – RS256, ES256), token formats (JWT vs. JWE), certificate lifetimes, revocation mechanisms.
-
Agents and services must enforce these policy constraints dynamically: rejecting interactions that do not align with the metadata-stated policy chain.
Technical Interplay with Other Standards
-
PKI / mTLS: Agent identities are backed by certificates or key-pairs; those keys are referenced in federation metadata. mTLS ensures channel authenticity.
-
OAuth/OIDC: Agents obtain JWT access or ID tokens; the issuer is a federated entity, and token claims reflect the agent’s identity, scope, delegation context.
-
Metadata endpoints: Agents/services publish
federation_metadatadocuments, signed and versioned, discoverable via well-known endpoints (/.well-known/openid-federation). -
Trust chains: Using JSON Web Signatures (JWS) or JSON Web Tokens (JWT) as metadata statements, trust is transitively verified: from trust-anchor → operator → entity → agent.
Design Patterns for Integrating Agentic AI with Federation
Here are a set of patterns and architectural considerations for embedding OpenID Federation with agentic-AI systems.
Agent Identity & Lifecycle
-
Each agent is assigned a unique entity identifier (URI form, e.g.
agent://host-service/agent-1234) and a key-pair or certificate. -
The host service manages agent creation, key rotation and revocation; it publishes metadata that includes agent identity, key-thumbprint/certificate, lifecycle status (active, deprecated).
-
Short-lived credentials: Agents should use ephemeral credentials (e.g., 1h token + certificate bound) to limit risk of compromised long-lived credentials.
Secure Invocation Pipeline
-
Agent invokes an API endpoint with:
-
mTLS client certificate (bound to agent identity)
-
JWT Access Token signed by the agent’s host’s authorization server, containing claims:
sub=agent://…,iss=host-service,aud=api-endpoint,scope=…,delegation_chain=[agent://…]
-
-
The API endpoint fetches metadata: checks the host’s federation metadata, verifies signature, checks certificate thumbprint, validates delegation claims, inspects the policy constraints.
-
Only once verified, the endpoint grants the agent’s request and logs the invocation (agent identity, call context, delegation chain).
Delegation & Sub-Agents
-
Metadata may include an attribute
delegatedAgentslisting identifiers of sub-agents and constraints (allowed scopes, max depth, expiration). -
A host spawns a sub-agent: the sub-agent gets its own certificate, token issuer issues JWT with
sub=agent://…,delegation_from=agent://parent. -
Up-chain verification: When sub-agent calls API, the API endpoint validates chain: parent metadata → sub-agent registration → verifying that allowed scope is within parent’s allowed scope.
Federation Onboarding & Discovery
-
When a new service joins the ecosystem, it fetches the federation operator’s root metadata, validates signatures, downloads the set of approved entities and policies.
-
The service uses the discovery endpoint (
/.well-known/openid-federation) of the host or agent to obtain its metadata, validate it and cache trust relationships. -
Trust revocation: If an agent or host is compromised, metadata can be updated (status=revoked); the cache must support update/fetch mechanisms (e.g., refresh intervals, push notifications).
-
Automated onboarding: The host service can self-register via API with federation operator, obtaining signed metadata; the service’s API endpoint can automatically discover and trust that host’s agent set.
Audit, Provenance & Accountability
-
Since agentic AI often acts without human oversight, audit trails must record: agent identifier, host service, delegation chain, timestamp, API call, outcome, version of agent (model id, training data hash if relevant).
-
The federation metadata can include optional fields such as
agentVersion,modelId,certificationLevel, enabling downstream services to enforce policy: e.g., disallow unverified agent versions or require human-reviewed agents only. -
The identity layer becomes the provenance anchor: Every action maps to an agent identity, tied to the federated trust chain — enabling incident response, forensics, and compliance.
Practical Considerations & Implementation Tips
Metadata Caching and Refresh
Federation metadata is a living artifact — it changes as keys rotate, policies
evolve, or participants are revoked. Agents and services must therefore maintain
mechanisms to keep local trust data current. Implement ETag or Last-Modified
headers, schedule periodic metadata refreshes, and consider event-driven updates
such as cache-purge triggers or push notifications over WebSockets. The shorter
the propagation window, the smaller the risk of trusting outdated or compromised
entities.
Algorithm Agility
Cryptographic algorithms evolve, and federation metadata declares which ones are supported across entities. Both agents and relying services must negotiate and transition algorithms gracefully — for instance, maintaining compatibility with RS256 while preparing to migrate to ES256 or EdDSA. Key rotation should be performed methodically, ensuring signatures remain verifiable across the transition period.
Short-Lived Tokens and Certificate Binding
Bearer tokens alone are insufficient in autonomous systems. Every access token
should be short-lived and cryptographically bound to a client certificate
through the cnf claim. This enforces proof-of-possession semantics —
possession of a token without the corresponding private key becomes useless.
Combined with mTLS, this eliminates a major class of impersonation and replay
attacks common in AI-agent architectures.
Delegation Depth Control
Delegation chains must have explicit boundaries. Federation metadata should
define a maxDelegationDepth parameter, limiting how many generations of
sub-agents can be spawned under a parent. Runtime enforcement ensures that no
autonomous process can recursively delegate authority beyond policy limits — a
critical safeguard against uncontrolled agent proliferation.
Agent Versioning and Retirement
Agentic AI components evolve continuously — retrained models, logic updates, or
new decision heuristics. Federation metadata should reflect this through version
identifiers and lifecycle states such as active, deprecated, or
pendingDeletion. Before honoring a request, downstream services should verify
that the agent’s version is valid and approved within the federation. This
creates a clear operational boundary for phasing out outdated or insecure
agents.
Policy Enforcement at Runtime
Policies expressed in federation metadata — allowed scopes, endpoints, or hosts — must not remain static declarations. Services should enforce them dynamically for every invocation, rejecting requests that violate current policy constraints. This approach keeps access control adaptive to evolving operational requirements while maintaining centralized governance.
Compatibility with Enterprise Identity Systems
Organizations rarely start from a clean slate. Most already maintain internal PKI, LDAP directories, or SAML-based identity providers. OpenID Federation can serve as an overlay — a unifying metadata layer that federates existing trust anchors and standardizes discovery. Mapping agent identities to enterprise certificates enables gradual adoption without disruptive migration of legacy identity systems.
Revocation and Incident Response
Compromise and policy violations are inevitable; what matters is how quickly
they’re contained. Federation metadata provides an immediate control plane for
revocation. When an agent or key is compromised, update its metadata status to
revoked, invalidate related certificates, and notify the federation operator.
Downstream services must check metadata freshness on every authorization
decision to ensure revoked entities are never trusted beyond their validity
window.
Conclusion
The integration between agentic AI and OpenID Federation isn’t optional — it’s foundational. As agents span systems, domains and organisations, only a scalable, standards-based trust fabric will let them collaborate safely and effectively. Start by assigning identities, publishing metadata, enforcing lifecycle controls, and instituting federated onboarding — then layer in delegation, versioning and provenance.
If you’re building or scaling Agentic AI systems, now is the time to:
-
Assess how your agents authenticate, delegate, and access sensitive APIs.
-
Identify where static credentials, manual onboarding, or siloed policy enforcement create trust gaps.
-
Introduce OpenID Federation as the backbone for agent registration, metadata management, and verifiable access control.
The sooner your agents operate within a federated trust architecture, the sooner you can expand their autonomy — securely, transparently, and under continuous policy control. Federation transforms agentic AI from a collection of isolated automations into a governed ecosystem of accountable, interoperable digital actors.
Ready to Get Started?